Ensuring Information Security and Cyber Security is implemented, documented, measured and audited in your products, services and processes, resulting in business protection and successful ISO 2015 certification
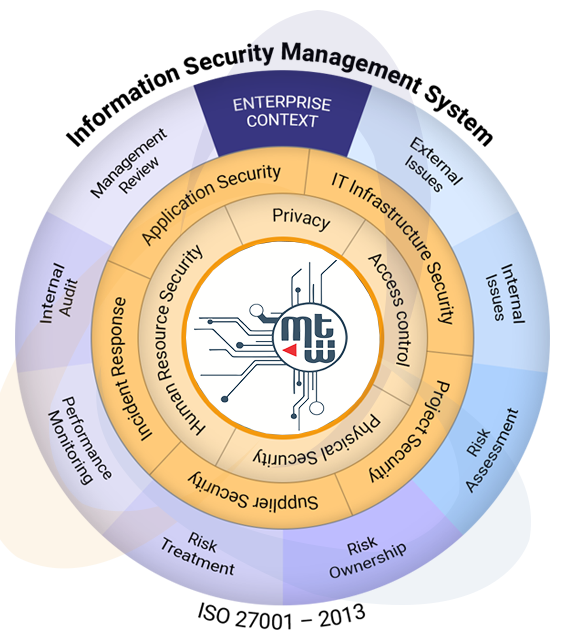
ISO 27001 Consulting Overview
ISO 27001 aims to protect information in all forms. We have a 7-phase approach that starts with understanding your business first, followed by information security objectives. This is followed by risk assessment and gap analysis - which helps us to recommend and advise you additional security controls. Our risk assessment is one of the most comprehensive assessment that includes all forms of assets that covers technology and non technology infrastructure and processes.
Each ISO 27001 consulting assignment results in transfer of knowledge, documented processes, and a framework that stays with the organisation. We believe in making ISMS simple, articulate, and easy to practice for all stakeholders, thereby gaining ROI on the invested subject.
We have implemented ISO 27001 for 100+ organisations that covered almost all business domains including Banking, Payment Card Processors, Telecom, Insurance, KPO, BPO, Manufacturing, Cloud Services Providers to name a few.
What makes us unique is our involvement in designing your implementation, securing your infrastructure, and reduction of risk. Other unique features involves our project management, our control design framework (5 folder structure per team), our comprehensive documentation, our explanation of each individual control to individual stakeholders, our 3 categories of risk assessment reporting, our 4 dimension tracking, our method of reporting business transactions for security, and ensuring zero defect certification.
Get Quote
WHAT IS ISO 27001: 2013?
The standard is divided into management system controls and annexure controls
Key Processes include the followings
Management System Controls (Clause 4 to 10)
- Clause 4 - Context of the organisation
- Clause 5 - Leadership
- Clause 6 - Planning
- Clause 7 - Support
- Clause 8 - Operation
- Clause 9 - Performance Evaluation
- Clause 10 - Improvement
Annexure Controls (14 domains 35 control objectives and 114 detail controls)
- A.5 Security policies
- A.6 Organization of information security
- A.7 Human resource security
- A.8 Asset Management
- A.9 Access control
- A.10 Cryptography
- A.11 Physical and environmental security
- A.12 Operations Security
- A.13 Communications security
- A.14 System acquisition, development and maintenance
- A.15 Supplier relationships
- A.16 Information security incident management
- A.17 Information security aspects of business continuity management
- A.18 Compliance
Our Approach to Successful ISMS - ISO 27001 Implementation
We bring our world-class experience in delivery ISMS ISO 27001 implementation leading to successful certification.
PHASE I - Understanding Business and Security Objectives
Understanding the business context and ISMS context.
PHASE II - Gap Analysis and Risk Assessment
Detail risk assessment/Gap analysis that includes asset identification, risk assessment, and existing control identification. As a result of new ISO 31000 requirement, we provide three dimensions of risk management.
PHASE III - Design and Documentation
Design - In this phase we help create a framework of compliance for the organisation, in which every team in the scope has their respective controls, policies/procedures, access control, business/security transactions and communication methods.
PHASE IV - Tracking
4 Dimensional Tracking - We track your risks, we track your documentation, we track accountability of controls, and completion of individual ISO 27001 controls.
PHASE V - Control Measurement
Performance Monitoring - We determine whether the controls that are documented are performing using a 0-100% score.
PHASE VI - Internal Audit
Internal Audit involves verifying the effectiveness of the implemented controls through interviews and checking of all applicable controls.
PHASE VII - External Certification Support
ISO 27001 Registration body certification. This has is two stages:
1 - documentation, and
2 - implementation verification.
We support you in all the above phases to build a comprehensive ISMS.
Training
We provide bespoke training, listed below are our offerings.
- Shorter Sessions from 1 hour to 4 hours
- Interpretation of the ISO 27001 requirements
- 1 Day Awareness Session
- 2 Days Internal Audit Course
- 3 Days Implementation Course covering 10+ hands on exercises
Get Quote
Documentation Toolkit
ISO 27001 requires documentation of policies, procedures and records. As a result of several consulting assignments, we have some of the best content available that covers all the requirements.
Our documentation has the following salient features:
- Alignment with all ISO 27001- documentation requirements
- Our experiences turned into documentation templates
- Project Tracking tools to support the implementation
- Q & A support
Internal Audit
An independent assessment helps to assess the state of compliance. Our internal audit methodology includes people, process, technology and measurements to assure and provide management the degree of ISO 27001 compliance. Typically 3-5 days is required to perform a comprehensive internal audit.
Upon receiving your request, we will provide you further details.
Get Quote
Annual Risk Assessment
Risk Assessment is a mandatory requirement for achieving and maintaining ISO 27001. We have one of the most comprehensive risk assessments that comprises asset, controls and security policy objective wise risk assessment. Let us know if you are interested.
Upon receiving your request, we will provide you further details.
Get Quote
Program Management
Our consulting methodology experience has helped us to understand – what it takes to design and maintain a successful ISO 27001 compliance. ISO 27001 Program managemen removes the compliance responsibility to an external team, whereas the management focuses on customer/business delivery.
We currently manage program management for customers who has one location to another set of customers who have more than 8 locations worldwide
Upon receiving your request, we will provide you further details.
Get Quote
Information Security ‘measurement’ System
We have a successful framework for measurement of ISMS. The measurements checks ISMS objectives, as well as control wise objectives to provide you a scoring method applied. The measurements help the organisation provide a performance analysis and take actions proactively.
Upon receiving your request, we will provide you further details.
Get Quote
Call or write to us at :
sales@microcen.comfor proposal / roadmap / information

